
Two WordPress plugins required by the premium WordPress WPLMS theme, which has over 28,000 gross sales, are susceptible to greater than a dozen crucial severity vulnerabilities.
The bugs might allow a distant, unauthenticated attacker to add arbitrary information to the server, execute code, escalate privileges to administrator stage, and carry out SQL injections.
The WPLMS theme is a studying administration system (LMS) for WordPress, used primarily by academic establishments, companies offering coaching, and e-learning suppliers. It additionally presents integration with WooCommerce for promoting programs.
Vulnerabilities in WPLMS theme
Patchstack vulnerability researchers discovered a complete of 18 safety points within the WPLMS and VibeBP plugins and current in a current report 10 of essentially the most important ones.
Right here’s a abstract of the failings impacting the WPLMS theme:
- CVE-2024-56046 (CVSS 10.0): Permits attackers to add malicious information with out authentication, probably resulting in distant code execution (RCE).
- CVE-2024-56050 (CVSS 9.9): Authenticated customers with subscriber privileges can add information, bypassing restrictions.
- CVE-2024-56052 (CVSS 9.9): Much like Subscriber+ however exploitable by customers with scholar roles.
- CVE-2024-56043 (CVSS 9.8): Attackers can register as any function, together with Administrator, with out authentication.
- CVE-2024-56048 (CVSS 8.8): Low-privilege customers can escalate to larger roles, similar to Administrator, by exploiting weak function validation.
- CVE-2024-56042 (CVSS 9.3): Attackers can inject malicious SQL queries to extract delicate information or compromise the database.
- CVE-2024-56047 (CVSS 8.5): Low-privilege customers can execute SQL queries, probably compromising information integrity or confidentiality.
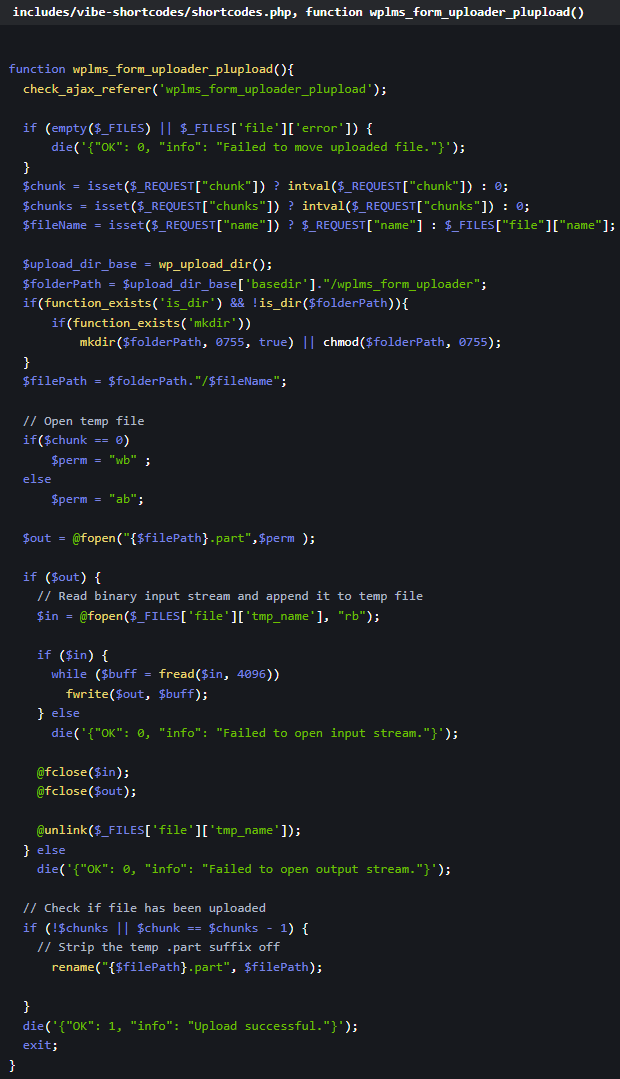
Supply: Patchstack
And for VibeBP:
- CVE-2024-56040 (CVSS 9.8): Attackers can register as privileged customers with out authentication.
- CVE-2024-56039 (CVSS 9.3): SQL queries could be injected by unauthenticated customers, exploiting poorly sanitized inputs.
- CVE-2024-56041 (CVSS 8.5): Authenticated customers with minimal privileges can carry out SQL injection to compromise or extract database info.
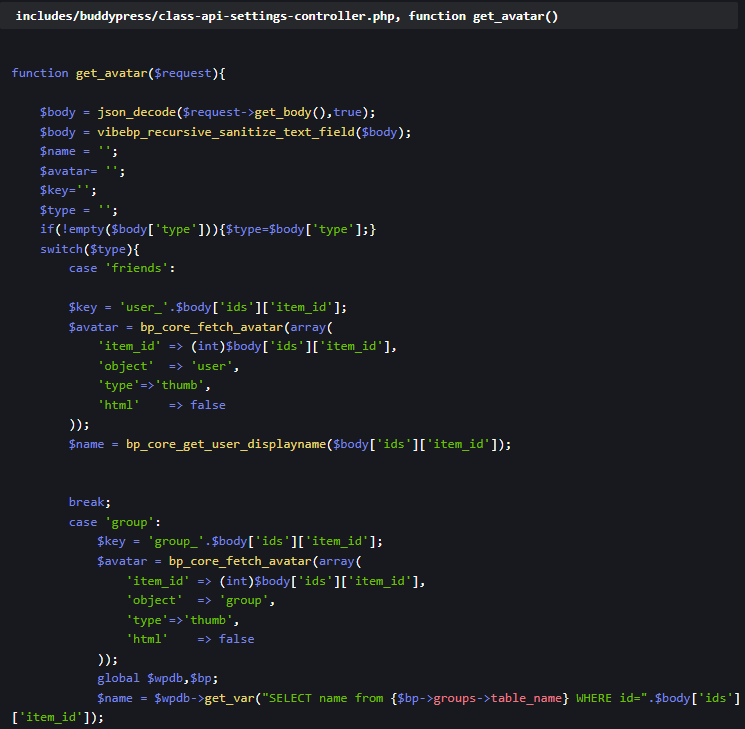
Supply: Patchstack
Customers of WPLMS ought to improve to model 1.9.9.5.3 and newer, whereas VibeBP ought to be upgraded to 1.9.9.7.7 or later.
As a basic safety recommendation, Patchstack means that web sites implement safe file uploads, SQL question sanitation, and role-based entry controls.
Patchstack discovered the vulnerabilities and on March 31 notified Vibe Themese, the developer of WPLMS, of the problems. Between April and November, the developer examined a number of patches till they had been in a position to repair all of the vulnerabilities.
Vibe Themes collaborated with Patchstack to guarantee that the delivered repair addresses all of the bugs.


